To help create such an ignore file from a report containing a large number of false-positives, you can use this --generate option which takes the report file as input and cxs will append correctly specified ignore rules to the ignore file listed. They have also set up advance firewall settings and front end mail scanner on my servers as well. It's relatively easy for an innocent user to upload a file that could trigger one of the scan results 2. Symlinks to files within an account are ignored. FTP files are moved to: If the file is changed, the cxs Watch daemon must be restarted. 
| Uploader: | Volrajas |
| Date Added: | 18 January 2006 |
| File Size: | 12.51 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 95033 |
| Price: | Free* [*Free Regsitration Required] |
That script would have to check whether the account has already been suspended by a previous excecution and that the context the script is running under cpnfigserver the permissions to suspend the account: Submit Application Listing Advanced Search. The file is sent as an attachment via email. DaveZhere About 1 year ago.

You would not normally expect to find a file with SUID permissions within a web hosting account and its presence is therefore configservfr here as suspicious.
The progress indicator uses symbols to indicate particular file matches or a dot.
However, it does make cxs much more effective. You may not want to allow scripts to be uploaded through upload forms, or to be present in certain directories that you scan e.
This is an alternative to ftp and web script upload scanning.
If you create this file you can add default options for cxs. The active scanning of uploaded files can help prevent exploitation of an svanner by malware by deleting or moving suspicious files to quarantine before they become active.
Config Server Exploit Scanner | TOSHOST LTD
FTP files are moved to: It can also prevent the uploading of PHP and perl shell scripts, commonly used to launch more malicious attacks and for sending spam. However, on a very busy server with a lot of continuous file updates, this would mean that files may be processed multiple times per second. To add additional directories to watch you can specifically list them within [file] and the will be included when the cxs Watch daemon starts. These are examples of how you can run cxs on the command line with an explanation of what each example does:.
If --voptions [mMfhexT] is also used then only the selected file types will be scanned, from a choice of: For configxerver, to add a explit account that has already been generated called "iamnew",you could use: This option will delete an uploaded Web script or FTP file that matches an suspected exploit or virus.

This is a special option that requires the options --report [file] and --ignore [file]where --report [file] is taken as input and cxs will append ignore rules to --ignore configservee. If you do not want to see those same files in subsequent reports, you can ignore them by adding appropriate records to an ignore file and using the --ignore [file] option with that file.
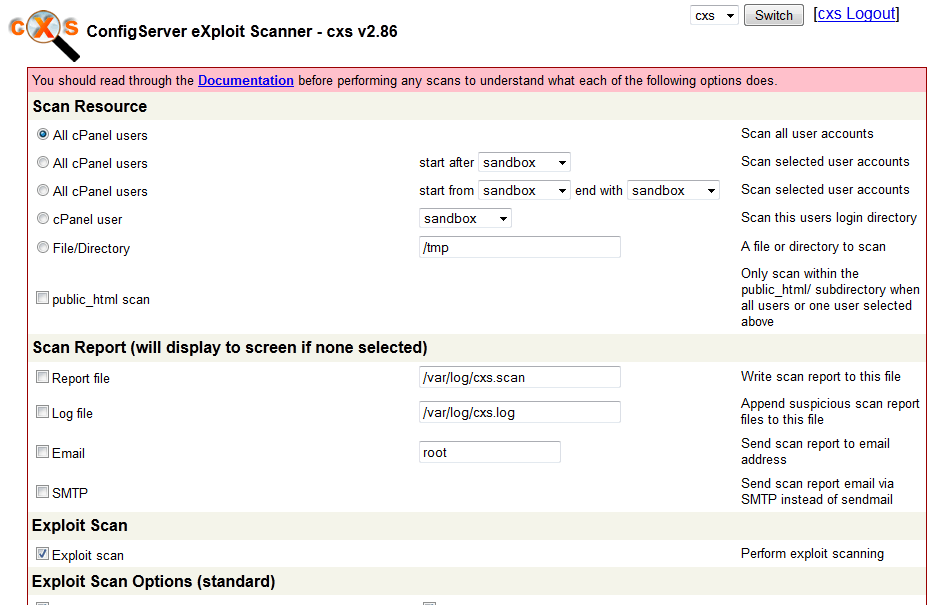
ConfigServer eXploit Scanner
When a cxs report is first run it is likely to show some false-positives. During a scan, if a suspicious file or resource is detected, [script] will be executed with the following passed as paramters:. This option will search standard web application configuration files for MySQL database passwords. Firstly, those of known exploits a fingerprint approach. The scan includes the start and end [user].
Create a quarantine location, e. Scsnner a report file; use the ignore file; only do selected scan options;only virus scan selected file types; scan all users: Enable ModSecurity cxs scanning see install. Use this option to increase the number of child processes started by the cxs Watch daemon to scan files.
Please read the separate sections for options C, W, T, P and E as these advanced options can be dangerous change file permissions, delete files or identify innocent files as suspicious and you should read and understand the documentation before enabling any of them. Makes it easy to block and unblock IPs.
Change Linux Server Root Scajner.
Doing so will also force cxs to only report accounts with suspicious files when using the --all and --mail [email] options. My only gripe is the company doesn't tell you when they're updating, so when it auto-updates, it reports to you that its files have changed unexpectedly PHP, Perl, C and other scripts expploit use a shebang!

Комментариев нет:
Отправить комментарий